Graphiant’s data
sovereignty as a service
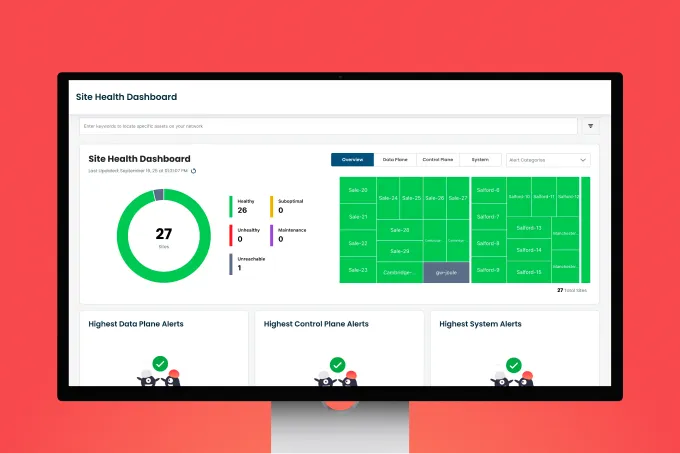
Geographic routing control. Enforce paths for sensitive flows. Approve or deny specific regions per application and tenant.
End-to-end encryption. Keys live at the edge. No decryption in transit. Data stays unreadable across the backbone.
Stateless core. The network forwards packets without storing or caching data, reducing exposure to foreign legal demands.
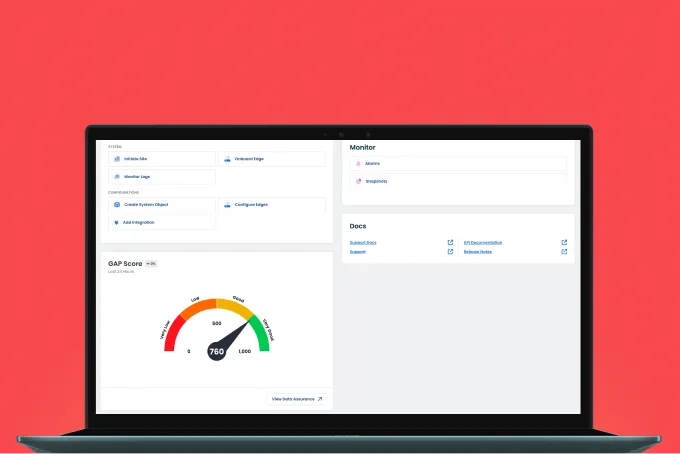


.webp)




